These Easy Practices Will Arm You against Email Threats
Phishing is the most widespread threat causing harm to smaller organizations, according to a recent survey. Yes, technology evolves and gets better at stopping malicious emails before they reach our mailboxes. But even if one email gets through and you fall for it, consequences can be devastating.
These basic practices will sharpen your ability to identify nefarious content in your inbox.
Carefully read the subject
Phishing emails usually instill a sense of urgency, starting with the subject line. For example, they can state that you will lose access to your email or banking account unless you take quick action.
Read the subject line carefully and be extra alert. If this is the case, your best move would be to skip the email altogether and either delete it or mark it as spam.
Check Sender’s and Reply-to Email address
Your next step is to check the sender’s email address, not just their name. Usually, you will see it right after the name of the sender, just like in the example below.
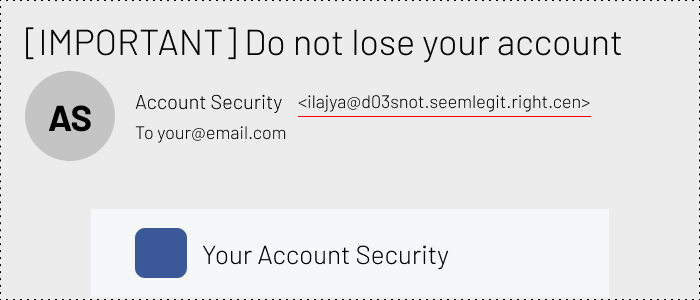 This is how you can check the real email address of the sender.
This is how you can check the real email address of the sender.
On mobile devices, you may have to long-press on the name of the sender to reveal the address the email has come from.
Once you see the email address, read it carefully – from the name of the sender (the characters before the “@” symbol) all the way to the last letter (the characters after the “@” symbol).
If the address is misspelled or unrelated to the context (for example coming from a Gmail account, but it refers to your bank), stop right there and delete the email.
Do the same checks against the Reply-to address.
Check web addresses before you visit them
Buttons and links in the email may take you to unexpected places. Before you click on them, hover with your mouse pointer and you will see the real address you will be visiting.
In the example below you can see that the real link looks suspicious, in contrast to the button it is attached to.
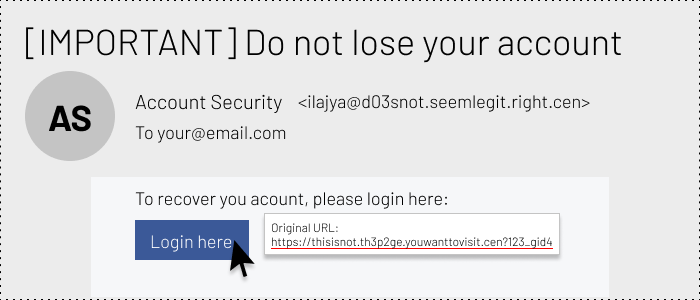 Тhis is how you can check the address a button or a link will take you to.
Тhis is how you can check the address a button or a link will take you to.
Often you see shortened URLs, such as https://bit.ly/34cfg5x, and you cannot really tell what page they will take you to, until you click on them. In such situations, tools like urlscan.io will help you see what is behind the short link. They will open and analyze the webpage for you to reveal potential threats. Once the scan is complete and if it is an address you are familiar with and feel sure about, you can open it.
Do not load external content unless you really need it to understand the email
By default, your email provider or email client may prevent external content such as images from showing up in your email. This is a basic security and privacy measure. Unless you really need to, do not load that content right away. The email may appear less inviting, but it should be readable.
Do not open attachments unless you are confident about the authenticity of the sender and you expect such an email
Before you open any attachments, first make sure the email is coming from a trusted source. Further, if the content has nothing to do with your work, you may just skip it.
When in doubt, ask
Even if everything else seems right, the request to open that file or transfer money to a different bank account may seem out of ordinary. Your best move is to confirm its authenticity with the sender over a different communication channel – in a call over the phone or by visiting the colleague.
Always doubt
Cyberattacks get more complex, advanced, and harder to identify with every day. All cybersecurity measures your organization takes aim at disarming them. But success and efficiency depend also on you and your abilities to identify threats and react accordingly.
You hold a powerful weapon against threats – doubt. It will keep your eyes open for the subtle details that always lurk in phishing attempts. Use it.



