Cisco Talos – the threat hunt as unique competitive advantage
Highlighting vulnerability spotlights in cybersecurity and conducting resilience guidance combined with qualitative intelligence is the fundament of Cisco Talos. Catching threats ahead of time in today’s hybrid environment is not an option, but a necessity.
Cybersecurity is a gigantic concept circulating within the dynamics of the IT world, taking an essential part of any customer experience. Cisco Talos being one of the biggest commercial threat intelligence services, not only offers qualified analysis but combines it’s excellent results with full-scale vulnerability research, rapid detection, and comprehensive protection against emerging and existing threats.
Full visibility and security posture clearing the status of the system leads means closing security gaps and mitigation of compromised endpoints. Observing anomalies in real-time and addressing securities issues before they become a threat enables organizations to deploy their IT infrastructure and keep their business operations intact.
The lifecycle of a threat determination is as follows:
- Defining the threat scope
- Initial analysis
- Detection
- Containment
- Eradication
- Recovery
How does Cisco Talos add to the competitive advantage of Cisco’s overall customer experience? It’s an ensemble of tools, processes, and intelligence solutions that deliver full scaled threat identification and prevention. It pinpoints security weaknesses and identifies a possible vector for compromises. Finally, it activates the organization’s incident response plan and mitigates the threat and risk as quickly as possible.
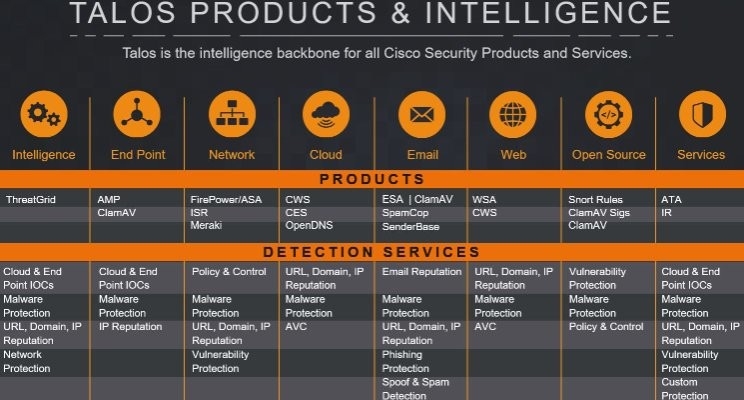
Advantages are created by the rapid time scope of Talos’ working process, an expeditive approach guaranteeing successful warfare against any security attacks.
Incident response – relationship-driven business
Incident response is one of the core stones of cybersecurity. A vital role of its success rate depends on a mutual, high-trust relationship between the threat hunters and the client. In other words, incident response is a relationship-driven concept based on mutual trust. A tested incident response plan designed according to client’s needs, accurately reflects critical capabilities, as evidenced in most cases. Talos has designed a detailed incident response retainer covering the full cycle of a potential threat.
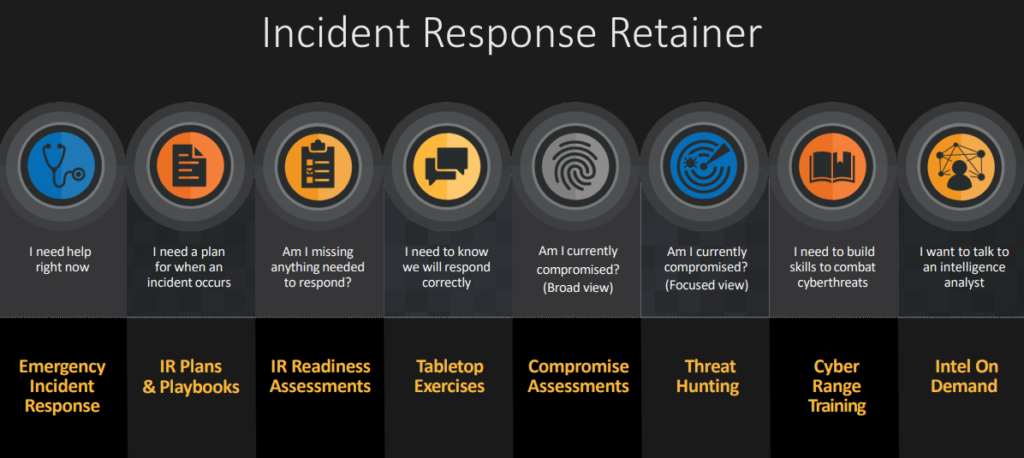
The relationship between external security experts and the client is tested during a cyber crisis. An elevated level of trust between them is essential. Resilience is successful only when and if there is an established and agreed-upon process strictly followed by both parties. Time is crucial when attacks are identified. Without synced actions, the chance of fighting the threat is critically minimized.
Fundamentally, the incident response is a crucial component to support the full life-cycle services as it’s one of the last pieces finishing the loop of fighting cyber threats. One of Talos’s greatest benefits is that it provides that significant extra step that follows advising the client about suitable actions when a threat is detected.
Besides the design, and execution of a tailored incident response plan, Talos also drives it’s clients toward resolution as quickly as possible. This rapid assistance is one of the major value-adding factors.
“Our Cisco Talos partners recognize the critical role relationships play in cybersecurity and Incident Response. The Talos Team has invested significant time and effort in us to fully understand our people and environment before an incident occurred. Together, we built familiarity and trust between our teams that can only be obtained through constant engagement and drills. When we were faced with a significant security incident, that trust, and familiarity were the key differentiators that enabled us to successfully contain the threat and minimize damages.”
CISCO customer
Designed for your specific needs – Talos and Telelink Business Servicess in sync
Telelink and Cisco Talos have similar visions, to see organizations as unique structures, something that creates significant competitive advantage and unites them making their partnership a long-lasting one. Provided services, expert guidance, and custom-designed plans associated with business capabilities are the strongholds of the partners. Identifying tangible processes involved with an incident response for each group within the organization lies as a fundament for securing the cyber environment. Analyzing the material and insights to build a customized plan is a must, before presenting the design for approval. Those steps are backed up by the determination of client’s goals and objectives for adequate threat identification.
Telelink and Cisco Talos approach every client from different angles when conducting a suitable security system. The defense against any attacks depends on the organization’s technology, functionalities, and on-prem expertise. Balanced relationships, an understanding of the business specifics and capabilities are the origin of tailormade solutions in cybersecurity. This baseline is embraced by both Telelink and Cisco Talos making their solutions winning ones.



